Windows Authentication
See also: User Authentication
Windows Authentication is
a user authentication option that is supplied with the system. When activated,
the Windows domain user name is used as the authenticated userid,
and optionally additional information about the user can be extracted from
Active Directory.
Windows Authentication is
configured as shown below using the User Authentication page of the
Server Admin App.
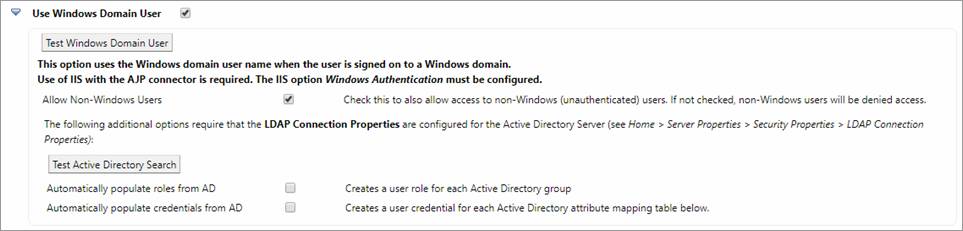
Prerequisites:
- The Verj.io server
must be running within a Windows domain.
- IIS must be used as a front-end web-listener
with users routed to the Verj.io server via the
AJP connector (or similar). The Windows
Authentication option within IIS must be selected.
Options/Buttons
- Test
Windows Domain User: This
button extracts the Windows user name of the signed on user and reports
it. If this test fails to return a user name, the prerequisites listed
above have not been correctly implemented.
- Allow
Non-Windows Users: when this
option is selected, users will be allowed access to the system even when a
Windows user name cannot be found. Typically you would select this option
if you wanted to mix both public and intranet users in the same system.
You could then limit access to internal administration forms based on
whether or not the user was signed on ( system.securityManager.isUserLoggedOn() ) or
whether they have certain roles ( system.securityManager.hasRole(roleName) ). When this option is not selected, only
valid Windows users will have access.
The
following options require that LDAP parameters are configured to connect to the
Active Directory server. This is done using the Security Properties page of the
Server Admin App. Caution!: the connection to Active Directory should be tested
before activating the options below.
- Test
Active Directory Search: This
button performs an Active Directory search using the currently signed on
user name, and reports a list of A/D groups found for the user. If this
test is successful the two options below can be safely activated. If the
test fails because of connection problems to A/D, the LDAP connection
parameters should be revisited on the Security Properties page of
the Server Admin App .
- Automatically
populate roles from AD: when
this option is selected, the system will connect to Active Directory and
extract all AD groups. A role is
created for each AD group. Roles can be checked by an application using:
system.securityManager.hasRole(roleName)
- Automatically
populate credentials from AD:
when this option is selected, the system will connect to Active Directory
and extract the named attributes and create a credential for each
attribute. Credentials can be checked by an application using:
system.securityManager.getCredential(credentialName)